
Imakatsu Soft Lure Huddle Swimmer 2.4 Inch RC ECO S-208 (7118) acquista in modo economico — spedizione gratuita, recensioni reali con foto — Joom

An illustration of the embedding and extraction process for the 2LSB... | Download Scientific Diagram

Joint index coding and reversible data hiding methods for color image quantization | Multimedia Tools and Applications
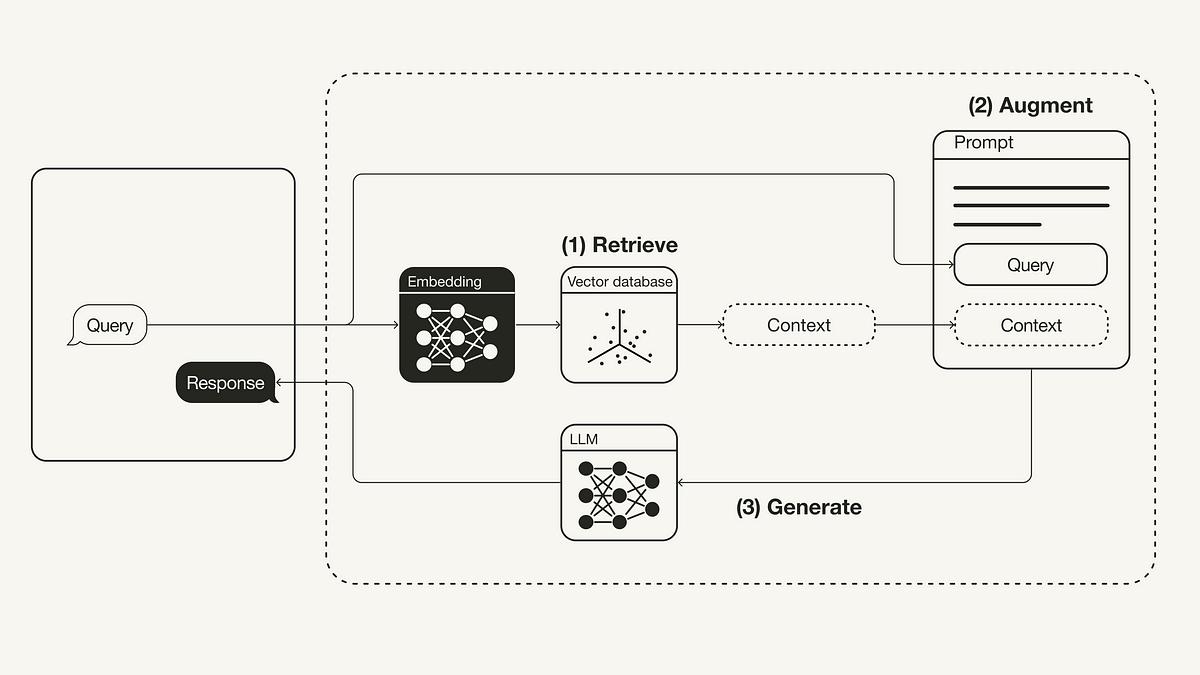
Retrieval-Augmented Generation (RAG): From Theory to LangChain Implementation | by Leonie Monigatti | Towards Data Science










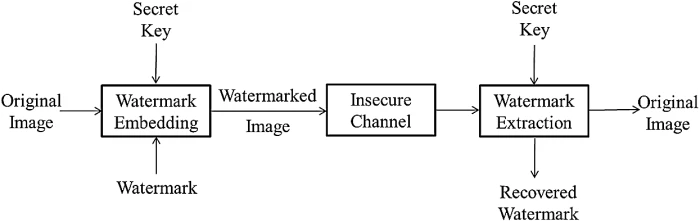






![PDF] IMAGE STEGANOGRAPHY IN YUV COLOR SPACE | Semantic Scholar PDF] IMAGE STEGANOGRAPHY IN YUV COLOR SPACE | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/04a613041a2f4d643bba17057b0d7a6e9e5f5c1d/2-Figure1-1.png)
