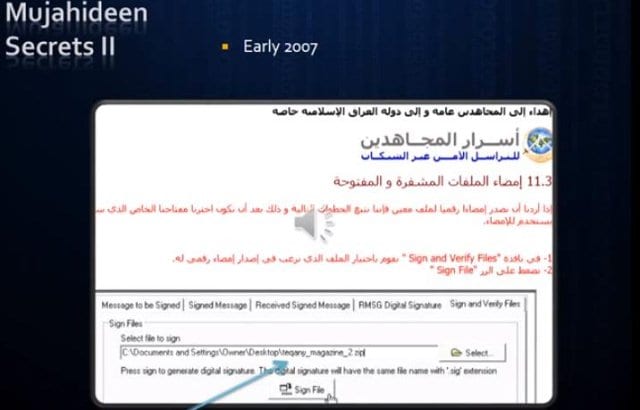
According to French "terrorism expert" Roland Jacquard, this manual, called "Mujahideen Secrets 2" is used by terrorists to avoid being tracked on the internet : r/programming

UK discussed plans to help mujahideen weeks after Soviet invasion of Afghanistan | National Archives | The Guardian

Al-Qaeda's Embrace Of Encryption Technology - Part II: 2011-2014, And The Impact Of Edward Snowden | MEMRI

An Afghan mujahideen guerrilla fighter with the Hezb-e Islami poses with his sword during fighting at the KHAD Secret Police compound in the capital April 15, 1992 in Kabul, Afghanistan. Following the

Indian Mujahideen: The Secret Jihad in South Asia: Krishankant, S. M.: 9789380318653: Amazon.com: Books