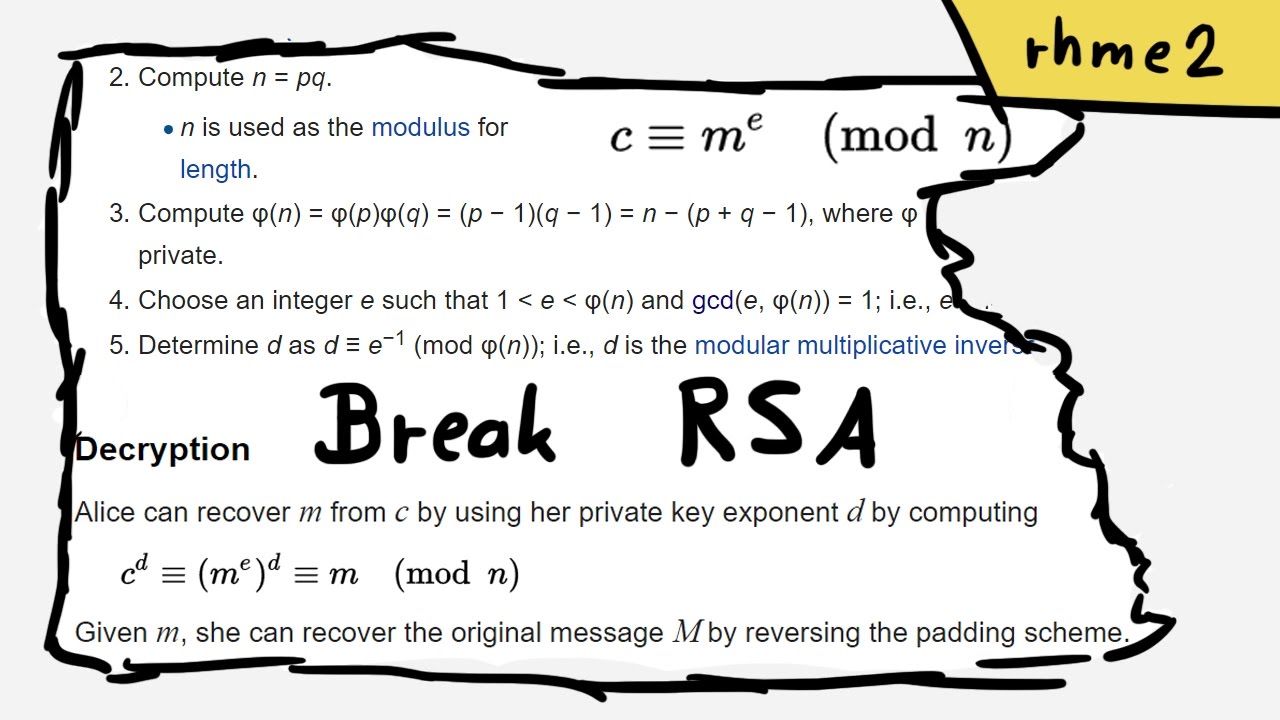
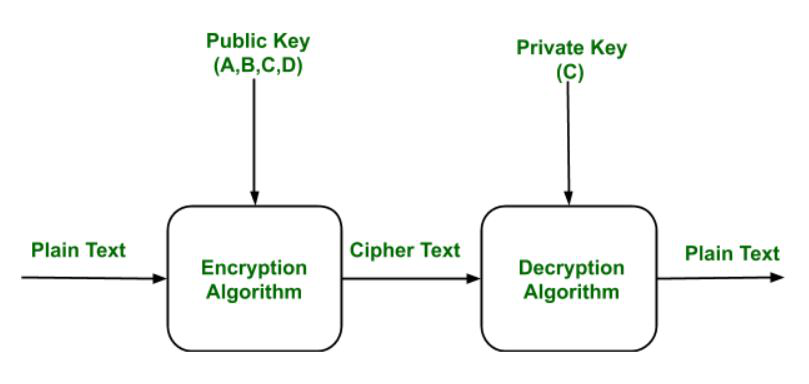
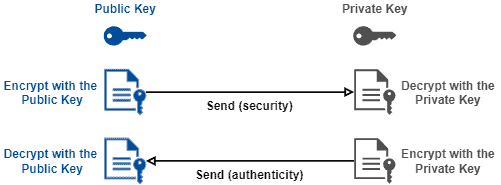
RETRACTED ARTICLE: An optimised homomorphic CRT-RSA algorithm for secure and efficient communication | Personal and Ubiquitous Computing
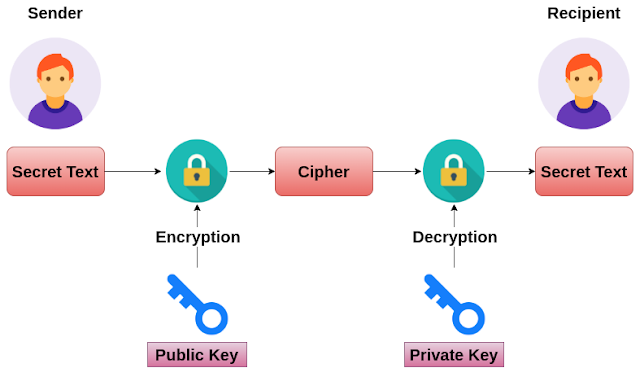
Unlocking Secrets: A Beginner's Guide to RSA Encryption and Decryption in Python | by Pronay Biswas | Medium

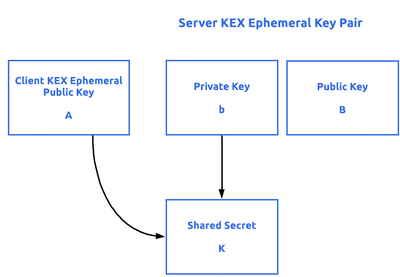
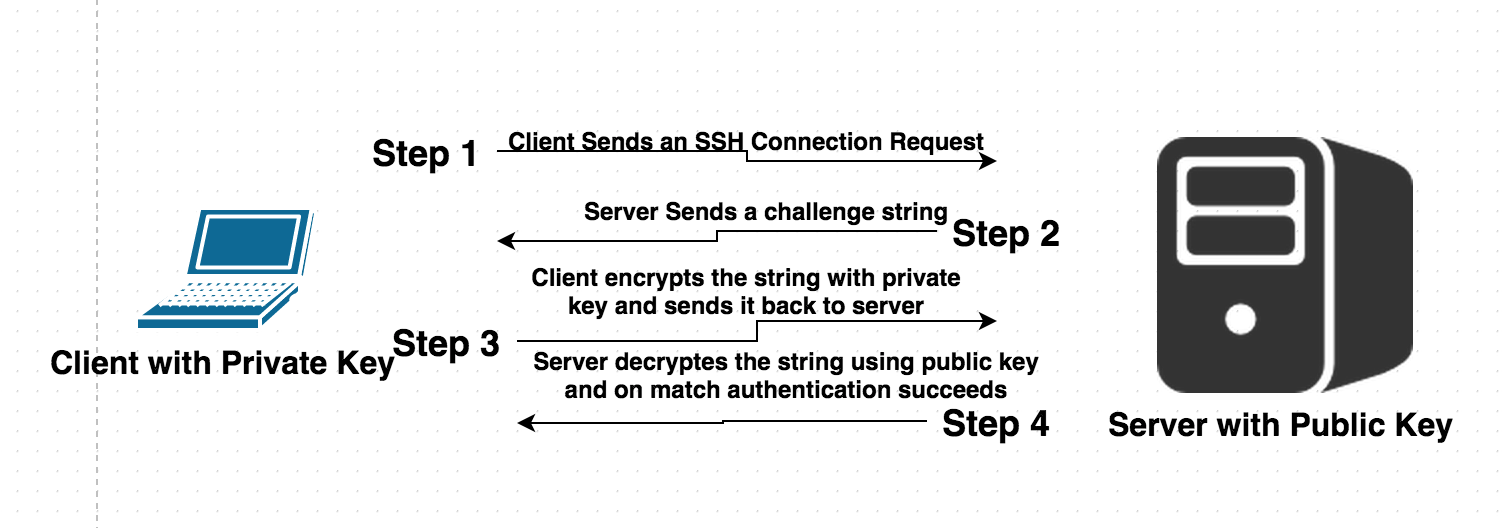
diffie hellman - Where is Challenge/Response and Certifcate Verification in TLS-DHE - Cryptography Stack Exchange